WiFi Assist is a new setting is meant to help your connectivity, but it could cost you money. In Apple iOS 9, there’s a new feature called Wi-Fi Assist. When you’re using a spotty Wi-Fi connection, it switches over to cellular
WiFi Assist is a new setting is meant to help your connectivity, but it could cost you money.
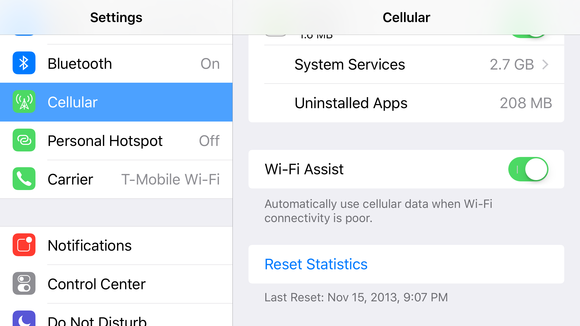
In Apple iOS 9, there’s a new feature called Wi-Fi Assist. When you’re using a spotty Wi-Fi connection, it switches over to cellular data. (Typically, your phone switches over to a cellular connection when Wi-Fi becomes unavailable. With Wi-Fi Assist, it kicks in when Wi-Fi meets what it deems as a “poor” connection.) If you have an unlimited data plan, it’s no big deal.
If you have a data cap or shared plan (most people do) you may unknowingly be using cellular data, and blow past your limit. That can cost money.
Access Wi-Fi Assist setting
- Tap the Settings app to launch it.
- Tap Cellular.
- Scroll all the way to the bottom, past the list of apps that use cellular data.
- You should find a setting for Wi-Fi Assist. You can switch off.
Tips on How to Identify a Phishing or Spoofing Email Hover over Friendly From Probably the easiest way to identify if an email is legitimate or not, is to simply hover your mouse arrow over the name in the From
Tips on How to Identify a Phishing or Spoofing Email
- Hover over Friendly From
Probably the easiest way to identify if an email is legitimate or not, is to simply hover your mouse arrow over the name in the From column. By doing so, you will be able to tell if the email is from a recognizable domain that is linked to the actual sender name. For example, an email from Match.com should typically have the from domain of “match.com” (not “motch.com” or “humbletemper.com”). - Are the URLs legitimate?
Continuing on with the theme of hovering over certain parts of the email, another place to check would be any URLs the email is directing you to visit. You will always want to make sure the link is legitimate. However, in order to be extra cautious, it is best practice to always open a new window and go to the site directly without using the email link provided in an email. - Incorrect grammar/spelling
A common practice of many hackers is to use misspelled words on purpose. While it may seem that this would easily reveal an illegitimate email, it is actually a tactic used to find less savvy users. Spammers have learned that if they get a response from a poorly written email, they are on to an easy target and will focus their efforts to bring that user down. - Plain text/Absence of logos
Most legitimate messages will be written with HTML and will be a mix of text and images. A poorly constructed phishing email may show an absence of images, including the lack of the company’s logo. If the email is all plain text and looks different than what you’re used to seeing from that sender, it is best to go with your gut feeling and ignore the message.
- Message body is an image
This is a common practice of many spammers. Make sure the email is a good mix of text and images. Also, there may be embedded links for you to hover over within the image for an extra step of precaution.
- Request for personal information
One tactic that is commonly used by hackers is to alert you that you must provide and/or update your personal information about an account (e.g., Social Security number, bank account details, account password). Phishers will use this tactic to drive urgency for someone to click on a malicious URL or download an attachment aiming to infect the user’s computer or steal their information.
- Suspicious attachments
Is this new email in your inbox the first time your bank has sent you an attachment? The majority of financial institutions or retailers will not send out attachments via email, so be careful about opening any from senders or messages that seem suspicious. High risk attachments file types include: .exe, .scr, .zip, .com, .bat.
- Urgent/Too good to be true
If an email seems too good to be true, it most likely is. Be cautious with any message offering to place money into your bank account by simply “clicking here”. Also, if the content places any kind of urgency as far as “you must click into your account now”, it is most likely a scam and should be marked as “junk”.
- Is my email address listed as the From address?
If you notice that your email address is being identified as the From address, this is a sign of a fake email message. Along those same lines, if the To field shows a large list of recipients, you should also be cautious. Legitimate emails will most likely be sent directly to you and you only. You may see “undisclosed recipients” and this is something to keep an eye on as well. It could be a valid send, but double check by using the other tips identified above.
Continue reading
Exercising the use of managed IT services benefits your business by increasing productivity, optimizing efficiency, and creating an easier way to achieve your business goals and plan for the future. Increase productivity with help desk services. Your employees shouldn’t be
Exercising the use of managed IT services benefits your business by increasing productivity, optimizing efficiency, and creating an easier way to achieve your business goals and plan for the future.
Increase productivity with help desk services. Your employees shouldn’t be
using their valuable time trying to diagnose a PC bug, troubleshooting a printer issue, or figuring out why they can’t access a network shared folder. Subscribing to help desk services allows your employees to focus on their business-related tasks and eliminates the constant worry of unforeseen technical issues.
Easily achieve your business goals by letting us manage your network infrastructure. Planning for growth, restructuring, and even moving offices can quickly consume all of your resources. By utilizing a managed IT services company to handle your network infrastructure and provide CIO services, your business will achieve peace of mind, allowing you to focus on making decisions that achieve your business goals.
Optimize efficiency by implementing software solutions. A couple of areas that businesses struggle with are redundant tasks and reporting. Software solutions allow your business to automate those redundant tasks and generate reports with button-clicks. Our software experts can quickly pinpoint areas in your business that can benefit from a software solution, and manage all aspects of implementation.
CIO as a Service – When your company needs a go-to person for everything technology-related. The benefit of CIO as a Service is value without the cost of a full time employee. You have someone that can make IT-related business decisions, supported by a team of experts that can efficiently deliver solutions. We are here all the time, but you only pay when you need us.
Hardware – When your company needs support for network hardware, printers, computers, and phones. The benefit of having a team of experts supporting your network infrastructure is reliability. Our team can monitor your systems to make sure everything is working properly all the time. Let us manage your network infrastructure so you can manage your business.
Software – When your business processes are hindering your ability to grow. The benefit of implementing software is efficiency. Automating redundant tasks, reducing data-entry, aggregating data, and reporting are just a few items that software solutions can provide. Our software experts have many years’ experience in providing solutions that allow our client’s businesses to grow while increasing the margin between revenue and overhead.
Help Desk – When you need support 24×7. The benefit of help desk services is that we are always here. When your computer crashes or a printer goes offline or your can’t access your network shared disks, you have a team of technicians to call that can quickly solve your problems.
About Net Inc
Based in Irving, TX, Net Inc’s IT tech support service provides small and medium businesses around the Dallas Fort Worth area with a comprehensive solution that enables business owners to concentrate more on growing their business and worrying less about IT.
NetInc is an IT consulting and support company that does 24/7 IT tech support, network infrastructure design and deployment, software consulting and development, and everything in-between. Net Inc is a team of unashamed tech-geeks who use common English terminology, who understand business principles, and are passionate about the relationships we have with our clients.
Continue reading
1. Reliability. Up to 71% of tape-based restores contain failures. Best Practice: Use disk-to-disk technology for backups. With disk-to-disk technology, your backup data resides on disk drives, proven to be far more reliable than tapes. When your backup completes, you
1. Reliability. Up to 71% of tape-based restores contain failures.
Best Practice: Use disk-to-disk technology for backups. With disk-to-disk technology, your backup data resides on disk drives, proven to be far more reliable than tapes. When your backup completes, you know the data is secure and accessible on the disk drive. With tapes you never really know if your data is usable until you try to restore it, at which point it’s too late.
2. Breadth of Offering. Choice in product and service offerings meet your business’ needs.
Best Practice: Don’t settle for less than what you need. Vendor offerings vary widely. Some are designed primarily for consumers and others for enterprise data centers. Choose a solution that scales (see scalability below), and offers the features you need to provide the level of service you expect. De-duplication and delta-block technologies will improve performance, reduce your data footprint and save you money. Choose a solution with block-level (not file-level) de-duplication. Look for block-level de-duplication. Make sure the solution can back up servers, PCs, and laptops as well your applications.
3. Security. 60% of organizations using tapes don’t encrypt their backups.
Best Practice: Get end-to-end encryption with no “back door.” Using encryption with tape makes backups run slowly and often takes too long to fit within a backup window. As a result, most people simply turn encryption off, creating a security risk. Even with the physical safety of disk-to-disk backup, encryption is essential. Look for 256-bit AES. Find a solution that encrypts your data during transmission and storage. Make certain there isn’t a “back door” that would let someone else view your data.
4. Accessibility. Companies waste thousands of hours waiting on tapes.
Best Practice: Ensure that you can get your data back with minimal delay. You should have direct access to your backups, with no time spent on physical transport (no trucks, no warehouses). Your restores should take minutes, not hours or days. Set yourself up to work with your data, not wait for it. Make sure your solution provider can meet your Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) which determine how quickly you can recover your data and maintain business continuity. Inquire about onsite and offsite replication that provide both improved performance and a solid disaster recovery strategy.
5. Scalability. Some backup systems can’t scale readily.
Best Practice: Invest in a data protection architecture that can grow with your business. You should be able to back up your data no matter how large it grows. Starting small? Look for an option that handles your backups automatically. Then, as you grow, gives you tools to manage complex environments. Look for “changes-only” and compression technologies to speed backups and save space. And insist on bandwidth throttling to balance traffic and ensure network availability for your other business applications. Make sure your solution relies on common technology to scale easily as your business––and data––grow.
6. Cost-effectiveness. Companies lose an average of $84,000 for every hour of lost activity.
Best Practice: Calculate the true total cost of tape-based backup. When you do the math, the dollars make sense: Go with disk-to-disk. Unlike tape, there are close to zero handling costs—no rush deliveries, loading, accessing, locating, or repeated steps. And there’s one benefit you can’t factor directly: Reputation. Reliability and security can make an incalculable difference with just one avoided breach or failure.
7. Compliance. Most companies have problems satisfying privacy, security, and data retention regulations.
Best Practice: Choose a data protection partner who has deep know-how about compliance, and the technology to ensure it. How do you recognize a strong compliance partner? They’ll gladly show you a table of regulatory requirements, and list for you how their products, services, and technology help you satisfy them. Even better: Use a vendor who successfully completes an SAS-70 Type II audit every year which helps you comply with regulatory requirements.
8. Disaster Recovery. Most companies lack a comprehensive, tested plan for disasters.
Best Practice: Find a vendor that delivers a complete DR solution. You can’t say your data protection is complete until you have a disaster recovery plan that is itself complete and tested. Your backup vendor should have both the product mix and professional services team to help you prepare for a worst-case scenario. Make sure they can help configure your backups so you rebound quickly. Best bet: A vendor who can train you to deal with disasters confidently, based on your company’s actual configuration.
9. Ease-of-Use. Some companies don’t—or can’t—manage their backups from one place.
Best Practice: Get control and reporting you can use anywhere, with ease. Managing your backup environment should be simple, and the software you use should eliminate any guesswork that could lead to lost data. You should know at all times if your data is protected across your entire network—including remote offices—by simply looking at a dashboard. The software should be simple to configure using wizards, yet powerful enough to meet your specific needs with customizable views, job propagation, and roles-based security.
10. Operating System and Platform Support. Most backup vendors support a limited range of OS, server types, and applications.
Best Practice: Look for broad and deep technology that supports your complete environment. Your backup solution should accommodate your environment, not vice versa. Demand a single solution to protect your laptops, desktops, and servers regardless of the platform and applications they’re running. Beyond the broad claims, check the fine print, and the level of protection offered for applications such as Exchange. For example, your solution ought to restore individual mail messages and contacts, and support Exchange running on a Microsoft Cluster.
11. Customer Support. Backup vendors’ product support varies widely.
Best Practice: Find a vendor whose support is passionate, maybe even slightly obsessed. Customer support should be one of your vendor’s main selling points. You shouldn’t have to wonder if they’ll be there to help when you need them most. Do they offer phone support or email only, are they available 24×7, and who exactly are you talking to when you call that 800 number? Find a vendor that will treat your data as if it were their own.
12. Reputation. Does your backup vendor have a quality reputation and the financial resources to stay in business for the long haul?
Best Practice: Find a vendor with strong financial backing and customer references. There are a lot of vendors that have come and gone. When you consider a service provider, look for one that has strong financial backing, a solid business plan and the ability to be in business as long as your data needs to be stored. Ask for customer references and case studies as their customers are the best validation you can get.
About Net Inc
Based in Irving, TX, Net Inc’s IT tech support service provides small and medium businesses around the Dallas Fort Worth area with a comprehensive solution that enables business owners to concentrate more on growing their business and worrying less about IT.
NetInc is an IT consulting and support company that does 24/7 IT tech support, network infrastructure design and deployment, software consulting and development, and everything in-between. Net Inc is a team of unashamed tech-geeks who use common English terminology, who understand business principles, and are passionate about the relationships we have with our clients.
Continue readingRegardless of who you choose for your hosted Exchange provider, you should not sign a contract without asking them these questions!! How many users do you support today? Service providers with only a handful of clients face an uncertain future.
Regardless of who you choose for your hosted Exchange provider, you should not sign a contract without asking them these questions!!
How many users do you support today?
Service providers with only a handful of clients face an uncertain future.
What does your SLA provide?
No one can provide a guaranteed 100 percent uptime so beware over-inflated promises or, conversely, providers with no written SLA.
How financially-sound is the hosted service provider?
If a hosting company disappears, your Exchange implementation is at risk.
What do current customers say?
Nobody knows a service better than existing clients, so make sure you get concrete answers to hard questions about reliability, access, customer service and any problems they’ve experienced.
Do you have Microsoft-certified technicians on-staff?
Your Exchange host should employ Microsoft-certified staff to ensure technological prowess and support. One reason you’re partnering with a service provider is to leverage their investment in highly qualified personnel.
Which in-house technologies do you use to support your hosted clients?
If a service provider doesn’t invest in its infrastructure, this does not bode well for the services it provides. Make sure providers are using top-tier vendors and the latest technologies.
What other services do you provide?
Finding a partner with multiple areas of expertise allows you to easily expand into other technology hosting agreements for money- and time-savers such as unified communications.
What migration tools are at my disposal?
A provider’s use of automated tools eliminates a lot of the necessary legwork, while live tech support ensures you’ll get answers when and how you need them.
How do you support after-hours email users?
Some service companies only have a skeleton crew, if any, after-hours. Since employees access email around-the-clock, it’s important that someone is always available to answer the phone if questions or problems arise. Therefore, 24×7 support is vital.
How do you support my end-users in different geographies or countries?
You don’t want agreements with multiple service providers; make certain your provider supports all the regions in which you operate – or look elsewhere.
Do you support mobile email users?
With more and more people accessing email via their phones it’s critical that your service provider supports these users.
Are you PCI Certified?
Payment Card Industry data security standards – mandated in many states – encompass acquiring banks, Independent Sales Organizations (ISOs), processors, hosts, e-commerce and retail merchants, shopping carts and other merchant services providers. PCI is a set of requirements designed to ensure that companies that process, store or transmit credit card information retain a secure environment.
Do you offer Microsoft Exchange as a hosted service?
If not, how will the service provider support you when you decide to upgrade?
What is your average on-hold time for callers?
Obviously nobody wants to spend their time on-hold. If a company cannot quantify hold times, that should send up a warning flag.
How will you support me as I grow?
As you expand operations, can your service provider support more employees, more geographies and more technologies?
How do I control my data if I use your service?
Your data should belong to you, and this fact must be stated clearly in your agreement. Watch out for companies that may hold data hostage if their contract is not renewed.
Is any of the migration process automated?
Automation eliminates many time-consuming but necessary tasks, reducing the chance of errors and speeding up your hosted Exchange implementation. These tools allow you to learn from the combined experiences of your service provider, rather than demanding you duplicate efforts.
How do you help me migrate my end-users?
Some hosted Exchange businesses only offer a technical support manual. Look for a partner that provides telephone and online support, as well as automation tools for many processes.
How long does migration typically take?
It’s important that your migration can occur quickly so you can immediately reap the benefits of your hosted Exchange agreement. The more automation and live assistance available to you, the speedier the process will be.
About Net Inc
Based in Irving, TX, Net Inc’s IT tech support service provides small and medium businesses around the Dallas Fort Worth area with a comprehensive solution that enables business owners to concentrate more on growing their business and worrying less about IT.
NetInc is an IT consulting and support company that does 24/7 IT tech support, network infrastructure design and deployment, software consulting and development, and everything in-between. Net Inc is a team of unashamed tech-geeks who use common English terminology, who understand business principles, and are passionate about the relationships we have with our clients.
Continue readingNet Inc, a Dallas based IT Consulting and Managed Service Provider, has some great points for businesses that may be contemplating hiring a company to be their managed service provider. Would Your Business Benefit from Managed IT Services? Review these
Net Inc, a Dallas based IT Consulting and Managed Service Provider, has some great points for businesses that may be contemplating hiring a company to be their managed service provider.
Would Your Business Benefit from Managed IT Services?
Review these business needs to decide if managed services can provide benefits to your business. If you answer yes to any of these, it can indicate areas where managed services could assist.
Continue readingThe best Backup and Disaster Recovery (BDR) Solution for small businesses Net Inc offers the only complete cohesive Backup and Disaster Recovery Solution (BDR) designed to backup multiple Windows Servers on and offsite. This solution will replace management intensive, error-prone
The best Backup and Disaster Recovery (BDR) Solution for small businesses
Net Inc offers the only complete cohesive Backup and Disaster Recovery Solution (BDR) designed to backup multiple Windows Servers on and offsite. This solution will replace management intensive, error-prone tape backups and external hard drives while providing much more. It’s completely automatic. With businesses depending more and more on the data stored in their servers, proper backups with data being moves off-site is becoming much more critical.
About Net Inc
Based in Irving, TX, Net Inc’s IT tech support service provides small and medium businesses around the Dallas Fort Worth area with a comprehensive solution that enables business owners to concentrate more on growing their business and worrying less about IT.
Net Inc is an IT consulting and support company that does 24/7 IT tech support, network infrastructure design and deployment, software consulting and development, and everything in-between. Net Inc is a team of unashamed tech-geeks who use common English terminology, who understand business principles, and are passionate about the relationships we have with our clients.
Continue readingMicrosoft Office 365 Microsoft Office 365 takes the industry’s most recognized set of productivity and collaboration tools — Exchange Online, SharePoint Online, Lync Online and Office Web Apps — and delivers them as a subscription service. With our cloud services,
Microsoft Office 365
Microsoft Office 365 takes the industry’s most recognized set of productivity and collaboration tools — Exchange Online, SharePoint Online, Lync Online and Office Web Apps — and delivers them as a subscription service. With our cloud services, your organization can lower overall costs and provide the (more…)
Continue readingIrving, TX,– Net Inc, a Dallas based Technology Consulting and Support Company, today announced it has joined Dell’s PartnerDirect program as a Registered Dell Partner. Built on three main tenets of simplifying IT, less complexity, and the advantages
Irving, TX,– Net Inc, a Dallas based Technology Consulting and Support Company, today announced it has joined Dell’s PartnerDirect program as a Registered Dell Partner. Built on three main tenets of simplifying IT, less complexity, and the advantages (more…)
Continue reading

